Control Costs with Policies
Terraform Cloud estimates costs for many resources found in your Terraform configuration. It displays an hourly and monthly cost for each resource, and the monthly delta. It also totals the cost and delta of all estimatable resources.
In this tutorial, you will enable cost estimation and define policy to check whether the total monthly delta is less than one hundred dollars a month.
This functionality is available in the Terraform Cloud Team & Governance tier, as well as Enterprise. Organization owners can enable a 30-day free trial in their settings under “Plan & Billing”. Cost estimates are not available for workspaces using versions of Terraform less than 0.12.0.
Prerequisites
For this tutorial you will need:
- A Terraform Cloud Team & Governance tier account or a Terraform Enterprise account
- A GitHub account
- An AWS account to create example resources
You should also be familiar with how to create and destroy Terraform Cloud workspaces.
Do not apply this policy to a production workspace as it may impact your production environment.
Terraform Cloud will not estimate cost on runs or applies targeted against a subset of resources.
Fork the sample repository
Fork the sample repository, which contains an example Terraform configuration to provision an EC2 instance.
Navigate to the versions.tf file in your fork of the repository in the Github web UI, and click the pencil icon in the top right corner.
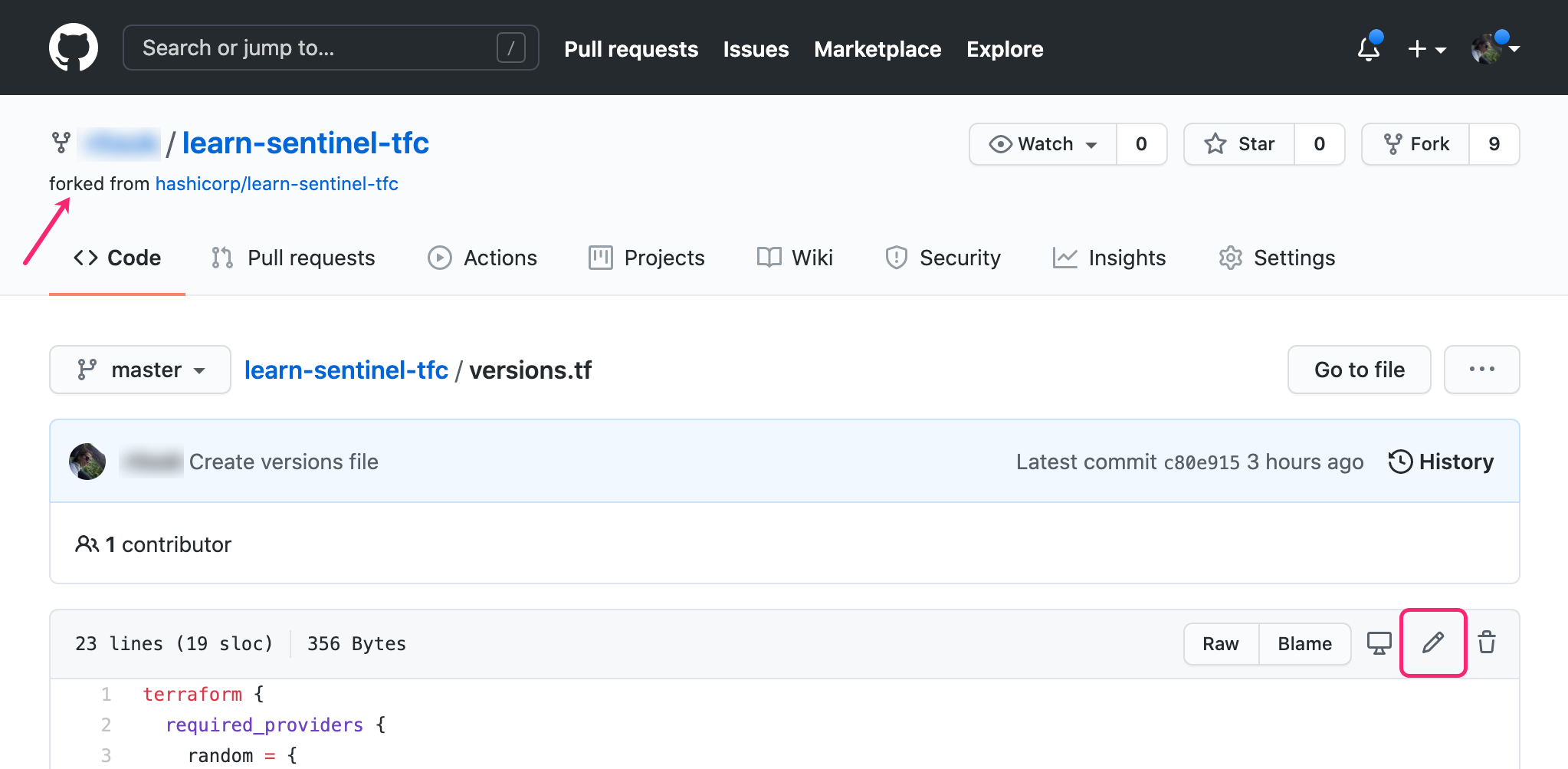
In the backend configuration block, replace "<YOUR_TERRAFORM_ORG>" with the name of your Terraform Cloud organization. Commit the change.
Create a Terraform Cloud workspace
Navigate to your Terraform Cloud organization and create a new VCS-backed
workspace connected to your fork of the learn-sentinel-tfc repository.
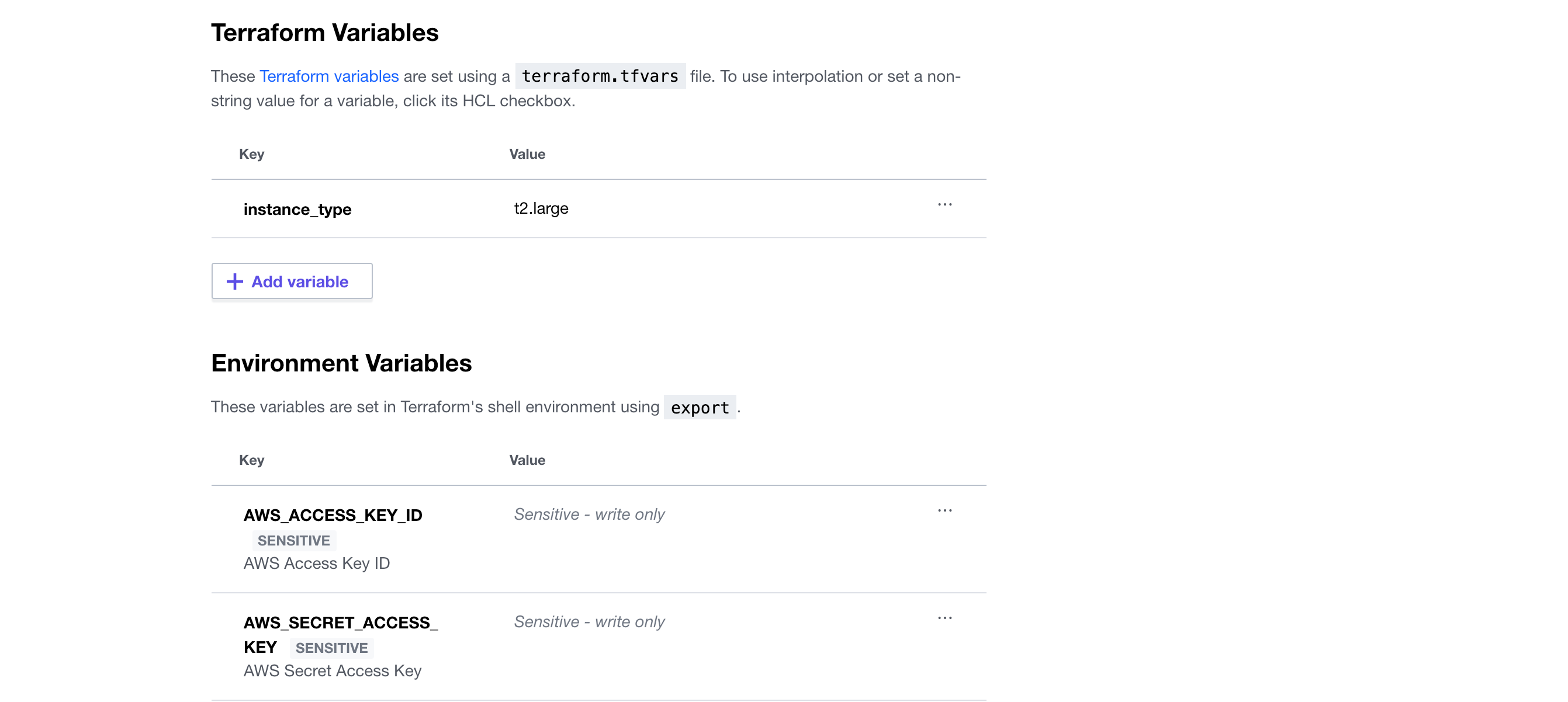
Configure workspace variables
- Navigate to your
learn-sentinel-tfcworkspace’s “Variables” page - Define a variable called
instance_typeand set the value tot2.large. - Define environment variables for your
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY. Be sure to set both assensitive.
When complete, your variable definitions will match the following:
Verify costs using policies
To verify cost estimates using policies, you need to define your policy and update your policy set.
Create a fork of the example repository, which contains a Sentinel policy that flags any resource changes that increase costs by greater than \$100.
The sentinel.hcl file in this repository declares the new policy in your policy set. Note that the enforcement_level is set to soft-mandatory: this allows team members with explicitly set permission to override the policy check and logs and overrides.
policy "less-than-100-month" {
enforcement_level = "soft-mandatory"
}The less-than-100-month.sentinel file contains the policy definition.
import "tfrun"
import "decimal"
delta_monthly_cost = decimal.new(tfrun.cost_estimate.delta_monthly_cost)
main = rule {
delta_monthly_cost.less_than(100)
}This policy uses the tfrun import to check that the cost delta for a Terraform run is no more than \$100. The decimal import is used for more precise calculations when working with currency numbers.
Terraform Cloud will run checks for policies defined in sentinel.hcl in all workspaces associated with the policy set.
Create a policy set
In Terraform Cloud, navigate to “Settings” > “Policy Sets” and select “Connect a new policy set”. Configure your fork of the learn-terraform-cost-estimation repository as the source.
The search bar for policy repositories is case sensitive.
In Terraform Cloud, you can apply policy sets either across your organization, or to specific workspaces.
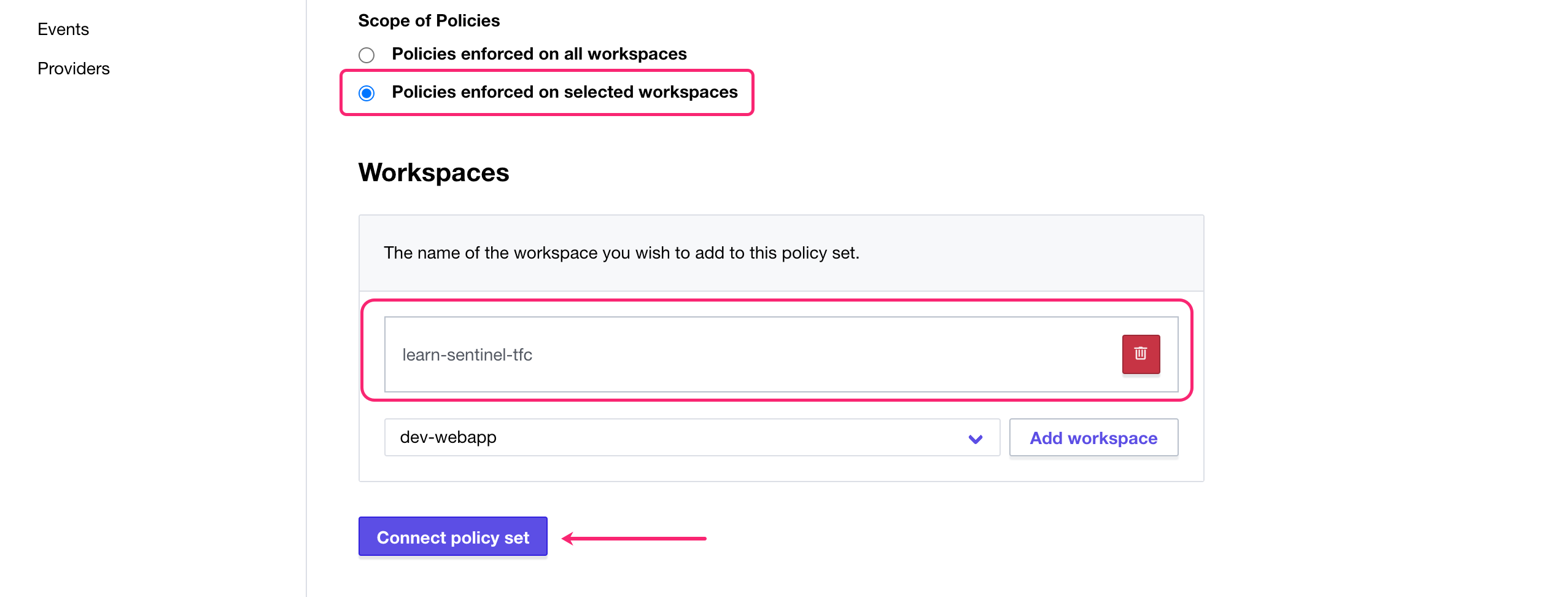
On the “Configure Settings” page:
- Select “Policies enforced on selected workspaces” under “Scope of Policies”
- Select your
learn-sentinel-tfcworkspace and click the purple “Add workspace button” - Click “Connect policy set”
Trigger a run
For a full list of supported resources in Terraform Cloud cost estimation, refer to the AWS Cost Estimation Documentation.
Navigate to your learn-sentinel-tfc workspace. Select “Start new plan” from the “Actions” menu, and run the default “Plan (most common)” option.
View cost estimate
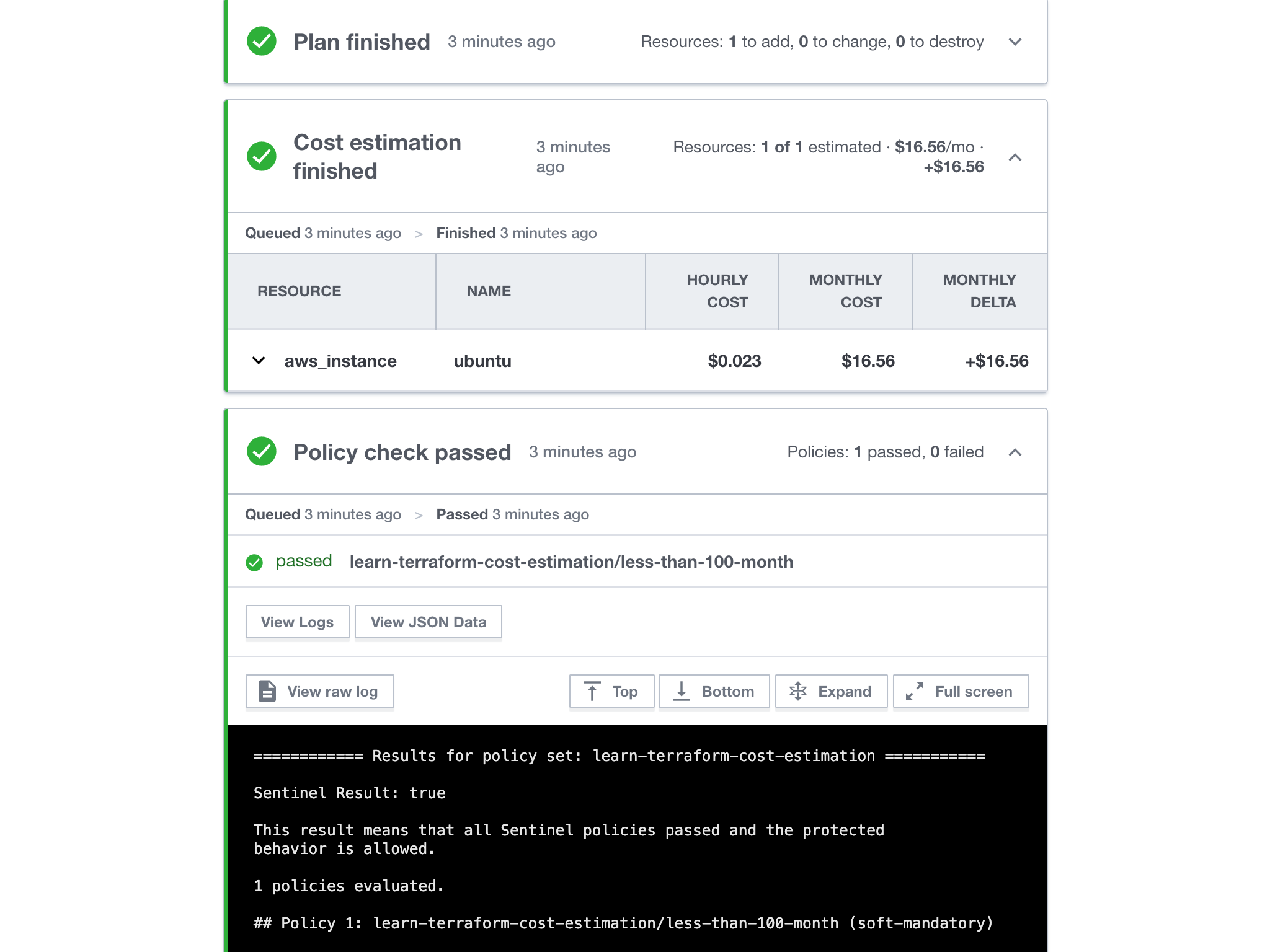
After queueing a new run, Terraform Cloud will estimate changes to your resource costs and display them in the run UI. There you will find the list of resources, their price details, and the list of un-estimated resources. You will also find the new total to determine the proposed overall monthly cost once the run is applied.
In this case, the new resource definition satisfies the Sentinel policy check you defined.
This is just an estimate; some resources do not have cost information available or have unpredictable usage-based pricing.
Click “Discard run” to cancel the run.
Delete the policy set
Navigate back to your policy set under “Settings” > “Policy Sets”. Under workspaces, click “Delete policy set”. Confirm by clicking “Yes, delete policy set”.
Delete workspace
If you do not plan on exploring other tutorials in this collection, you can delete the workspace you created. Terraform Cloud does not charge per workspace, so you are free to leave it if you would like.
Under your workspace’s “Settings” menu, select the “Destruction and Deletion” option and then delete the workspace.
Next steps
Congratulations - you have enabled cost estimation and used it in a policy check! This provides another tool to manage your infrastructure spending.
To learn more about cost estimation, refer to the Cost Estimation documentation.
If you would like to learn more about Terraform Cloud, refer to the following resources:
- Read the Terraform Cloud documentation
- Learn about the free and paid features of Terraform Cloud
- Learn more about Cost Estimation Documentation
- Read the Run States Documentation.